
Insider threats
It might sound like something out of a spy movie, but it is real, and it happens more often than you might think.
Insiders were behind 19% of all breaches according to Verizon’s 2023 Data Breach Investigations Report.
Types of insider crimes
When you think of insider threats, bad guys and intellectual property theft might come to mind. But threats come in all shapes and sizes.
The actions of well meaning employees can also lead to serious security breaches. For example, a sales person sharing sensitive product data and upcoming features in a bid to win business – ignorant to the fact that the “prospect” is a competitor. Or hospital staff accessing medical records of celebrities.

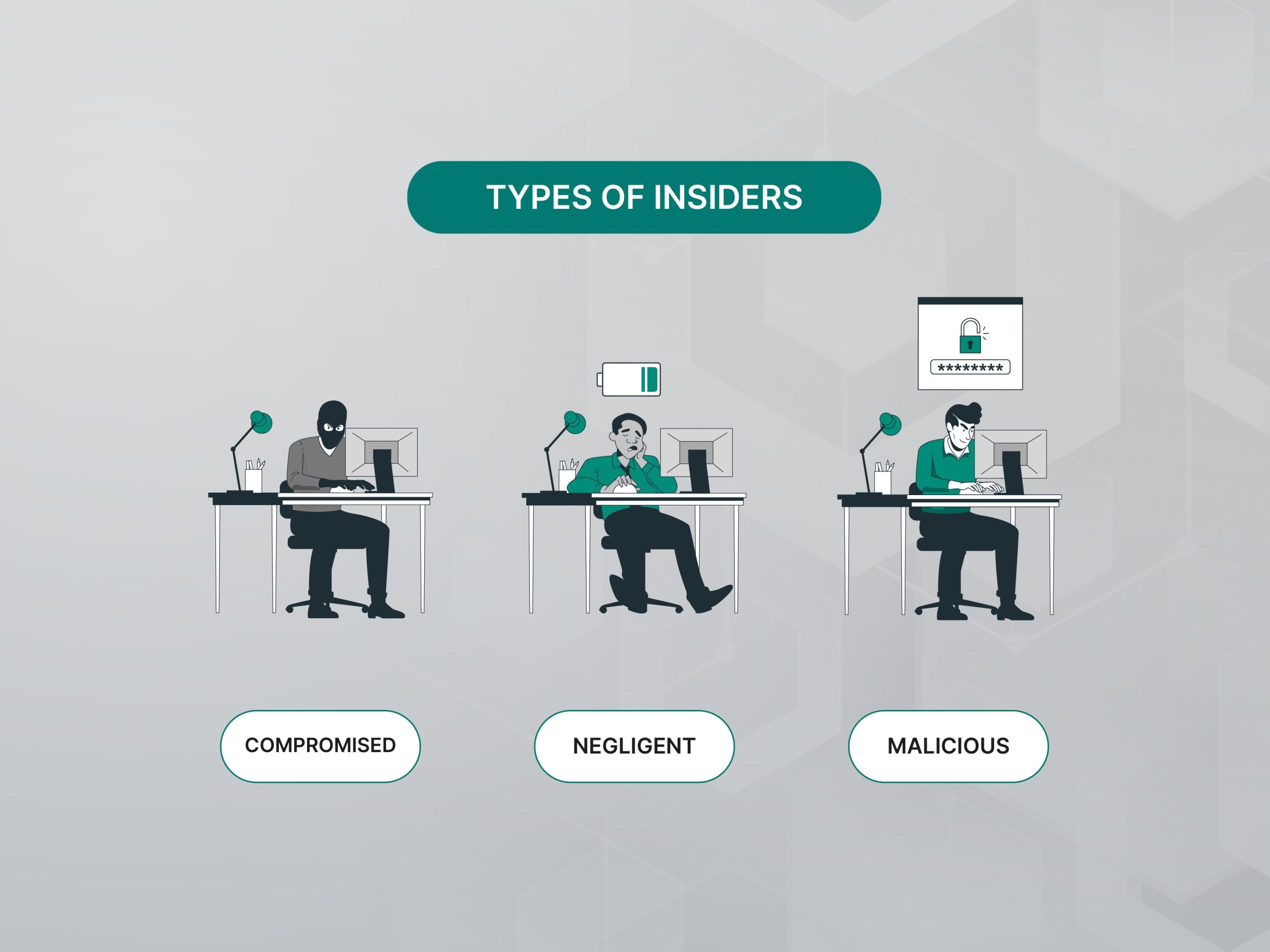
Who are behind insider crimes?
Negligent Insiders Staff who accidentally do things that put the company at risk. They might share data with outsiders, use weak passwords or click on suspicious links.
Malicious Insiders These are employees who have access to the company’s systems. They might try to mess things up on purpose or steal data, either to get back at the company or to make money.
Compromised Insiders These are bad actors who get hold of an employee’s login details and use it to to steal information or cause damage.
Besides these, external parties like vendors, contractors, and partners could also pose a threat.
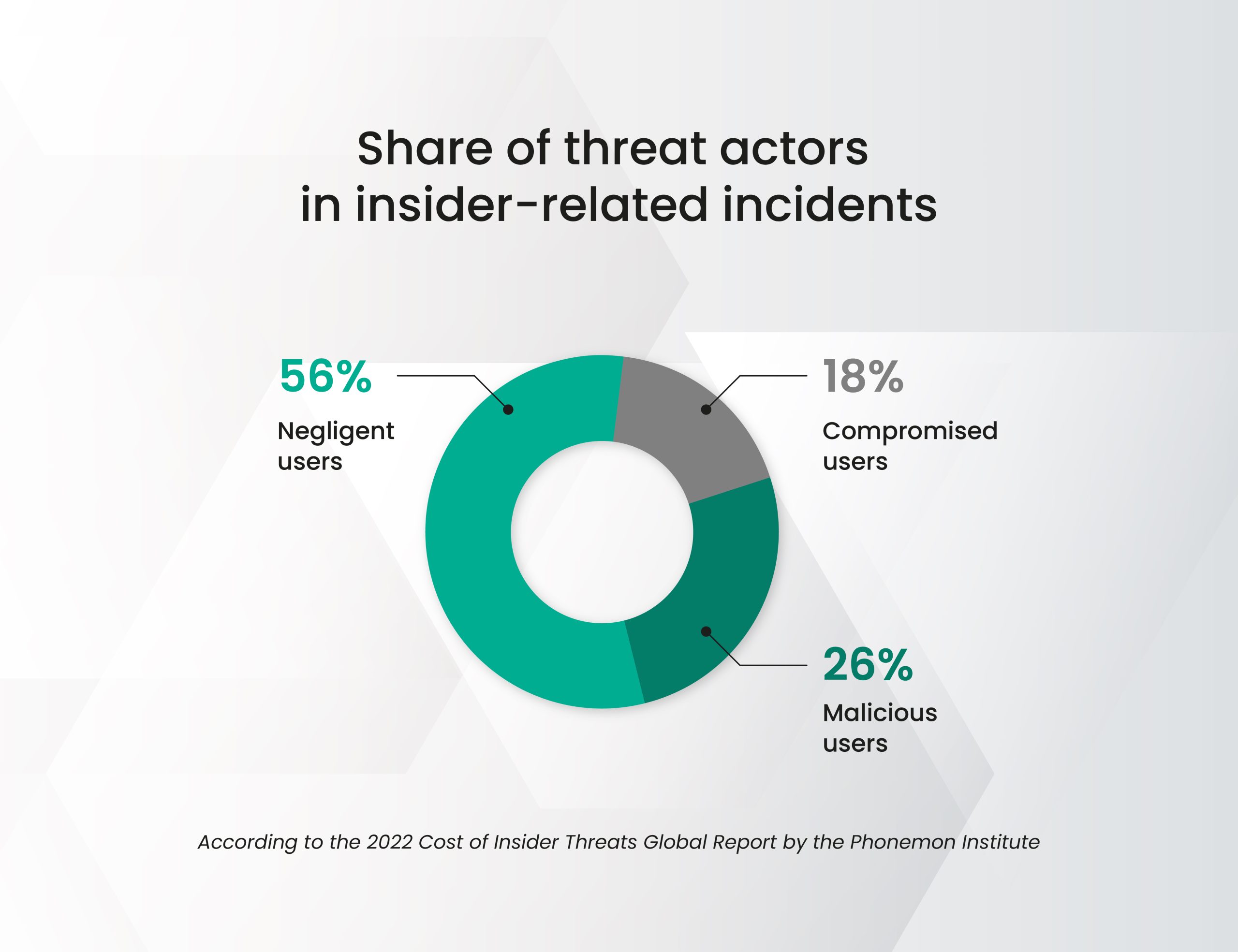
Share of threats
Malicious insiders and negligent employees make up the two most significant threats. These groups collectively account for more than 80% of all insider threats.

Categories of Malicious Insiders
1. Opportunists: They don’t plan malicious actions beforehand but seize opportunities as they arise. Warning signs include financial difficulties and past problematic behaviour.
2. Calculated attackers: These insiders meticulously plan their actions in advance, often targeting specific data. Detecting their attacks can be extremely challenging even after the fact.
3. Emotional attackers: Motivated by emotions like fear, greed, or anger, they strike impulsively without a detailed plan. Some even seek attention by getting caught, as seen in cases of disgruntled employees.
4. Terrorists and digital activists: Planning their attacks, they aim to cause maximum damage to corporate networks, sometimes without stealing data but by compromising infrastructure from within.
5. Friends and family: These insiders exploit their relationships to commit fraud or data theft, accessing the computers of acquaintances. This category is pertinent for managing subcontractors and remote workers.
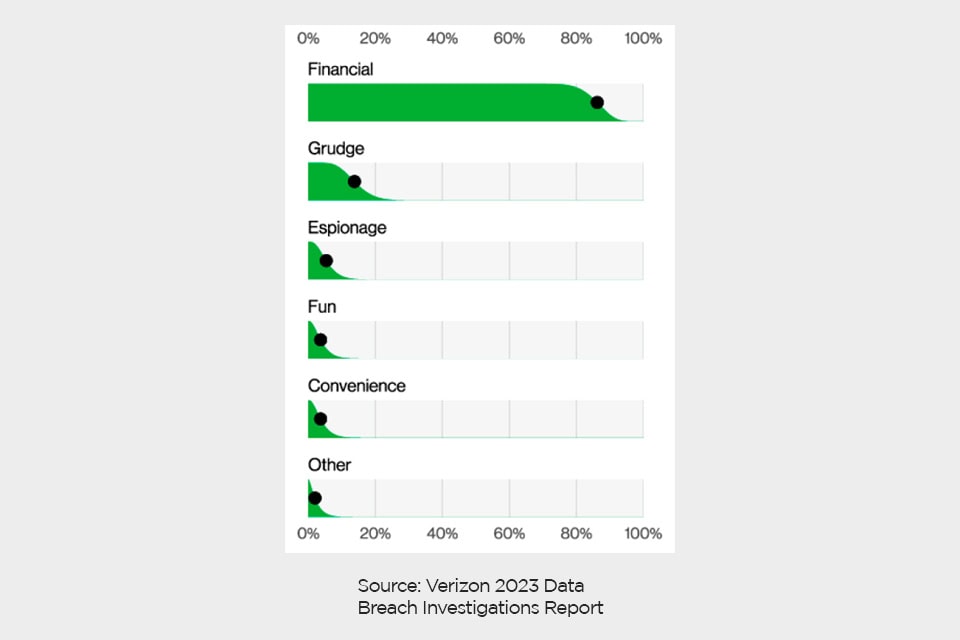
Motivation behind insider crimes
The most common motive behind malicious insider attacks are:
1 Financial gain
2 Grudge
3 Espionage

Mitigating insider risks
Insider threats are real. Here are some actions that can be taken to mitigate risk:
Companies
1. Monitor user activity to detect suspicious behaviour.
2. Control employee’s access to data
3. Conduct background checks
4. Cultivate a safety culture
Employees
1. Stay vigilant and report suspicious behaviour to IT/Security.
2. Follow company security policies.
3. Report lost or stolen devices
4. Be cautious when sharing sensitive information.
6. Attend cybersecurity training.
Want to learn more? Here are some great resources
Verizon’s 2023 Data Breach Investigations Report

