Highly targeted phishing attacks
Spear phishing is a sophisticated cyberattack method that targets specific individuals.
It can be highly effective and while spear phishing campaigns constitute only 0.1% of all email-based phishing attacks, they account for a staggering 66% of all breaches.
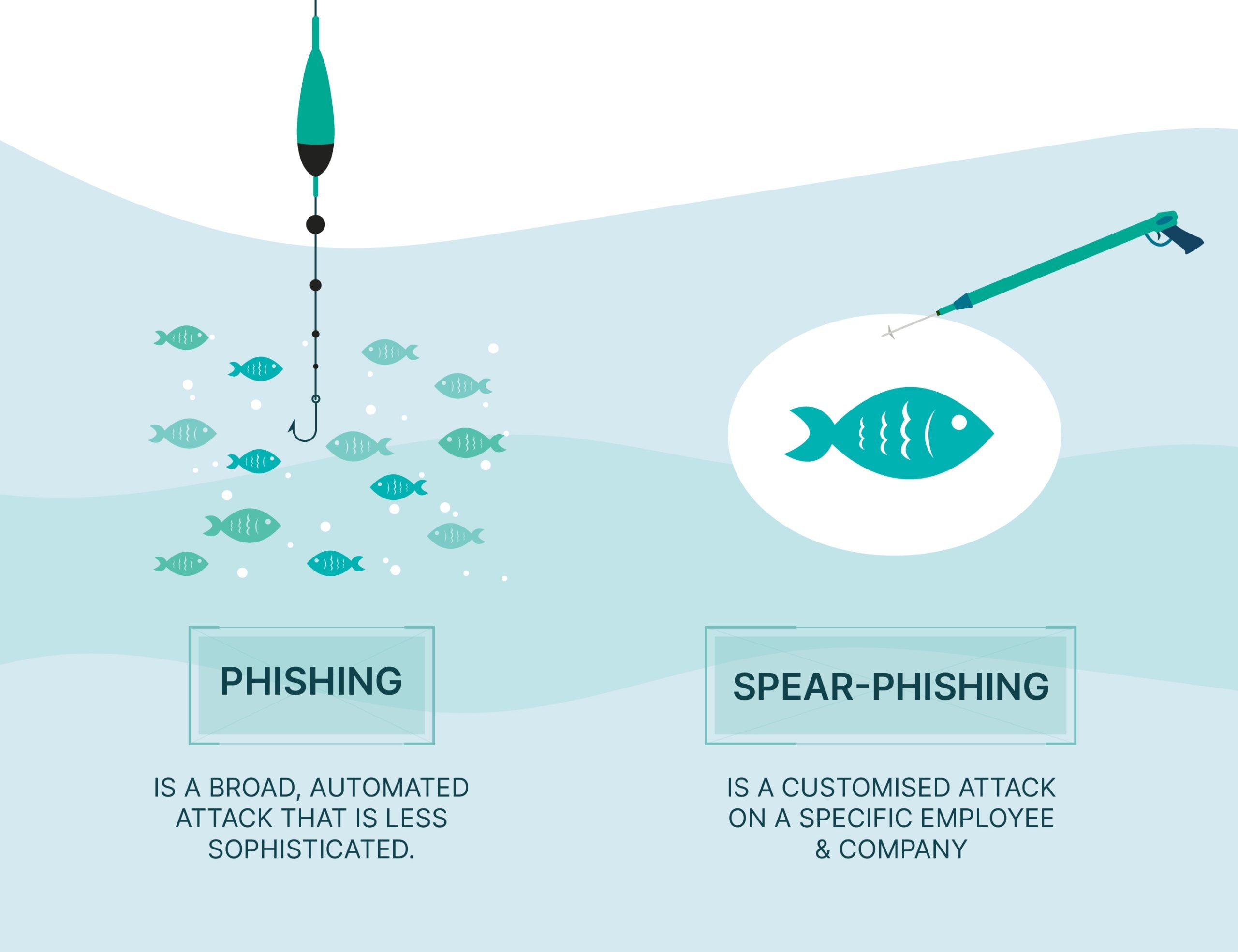
Spear phishing vs mass phishing
In contrast to mass phishing, which targets everybody with the same message, spear phishing utilises personal information to make the attack even more persuasive and realistic.
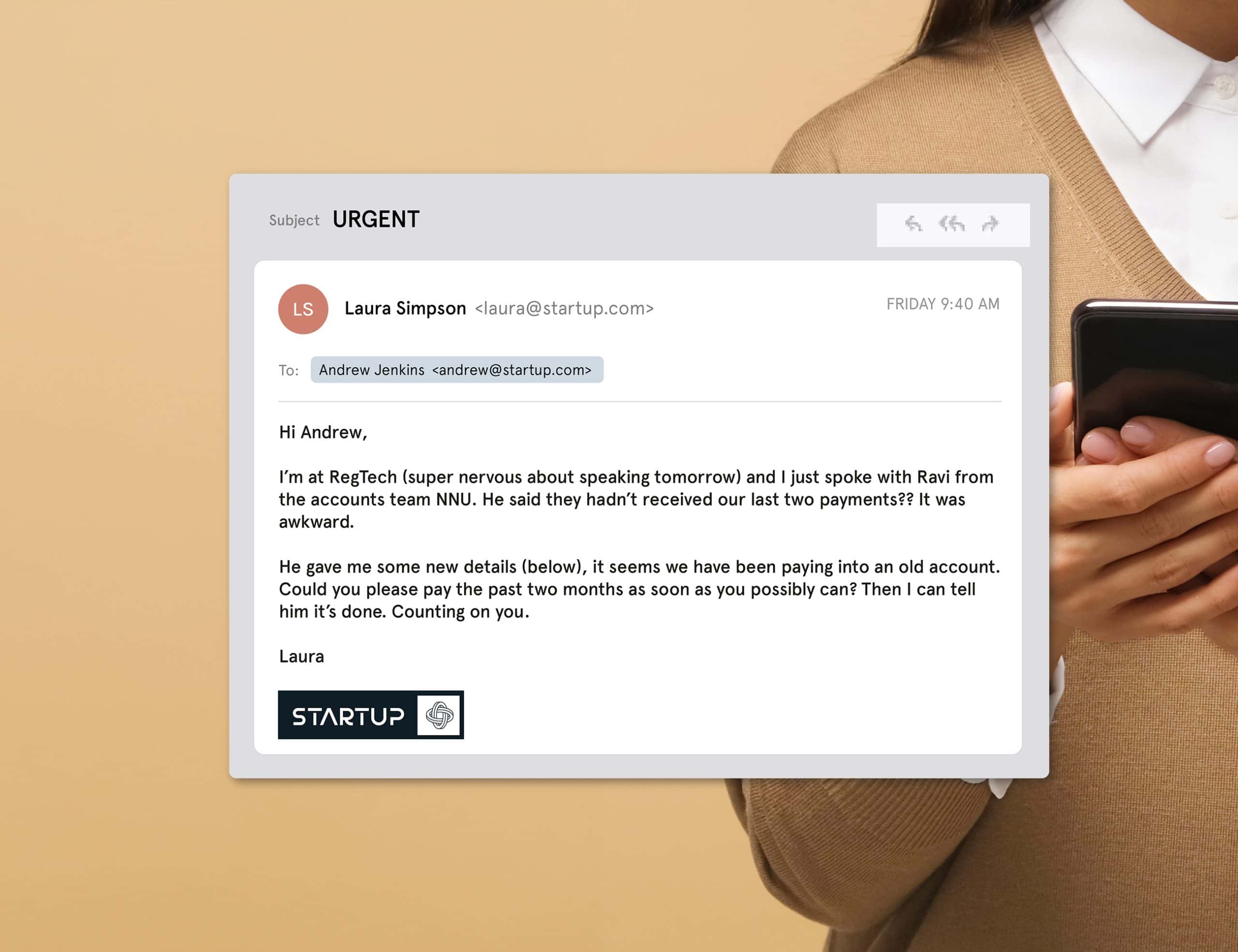
Example of spear phishing
The image shows a spear phishing attempt. The target is often contacted by someone posing as a trusted source. There’s usually a sense of urgency, and a bossy or threatening feel.
Invoice fraud
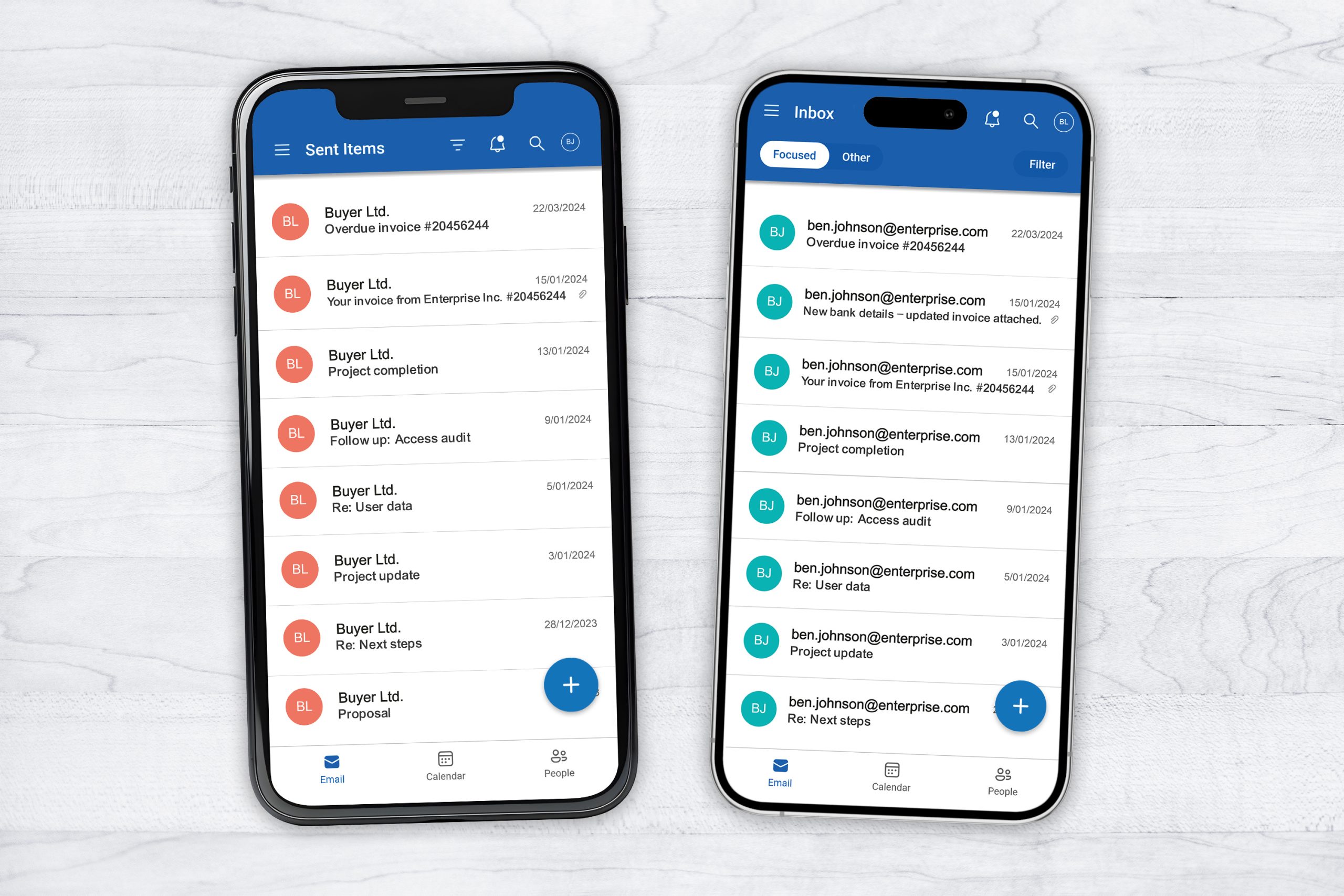
Here’s an example of a sophisticated invoice fraud attack
1. Through a breach on a different site, hackers got hold of a Ben’s (a sales person) password (which was reused across multiple accounts).
2. The hackers monitored Ben’s incoming and outgoing emails.
3. As soon as Ben sent the invoice to a customer, the hackers promptly designed a well made copy with new bank account details.
4. The hackers emailed the updated invoice (from Ben’s email account) and informed the customer that the payment details on the other invoice were outdated. This email was then deleted from Ben’s Sent items.
5. Subsequently, the hackers monitored the email inbox to ensure that no inbound emails questioning the change of bank details reached the victim Ben.
6. When the payment was made, the funds were transferred to the hacker’s account and were never recovered.

Targets of spear phishing
So, who are typical targets? Well, usually individuals who hold positions with access to information or funds. As you can see, that can include a majority of company departments!
-Finance and Accounting
-Executive Management
-Human Resources (HR)
-Information Technology (IT)
-Sales and Marketing
-Administrative (Assistants and Receptionists)
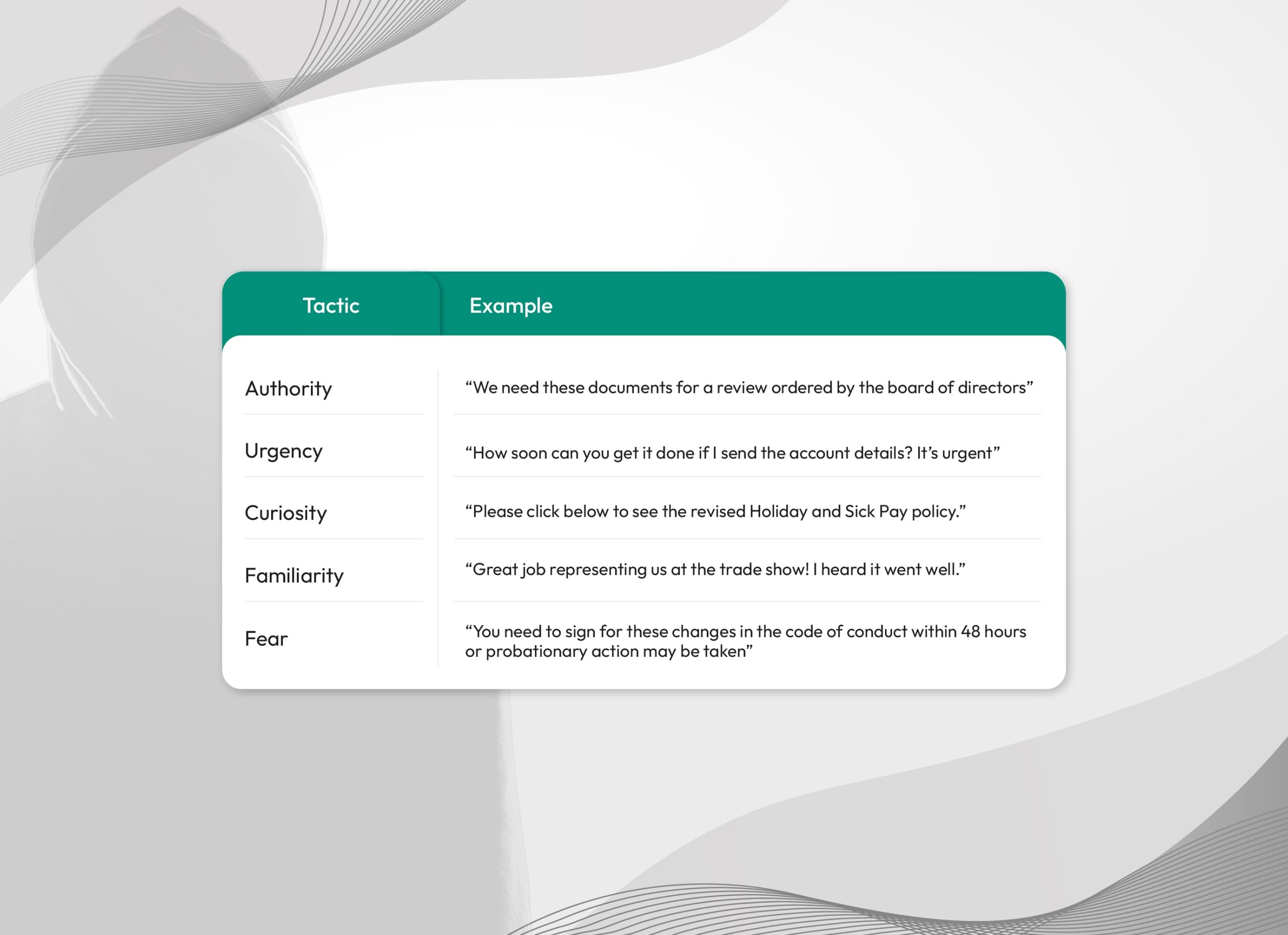
What tactics are used?
The image shows five tactics used by spear phishers, especially when it comes to CEO fraud.